This article will detail the steps needed to configure mutual TLS (mTLS) when sending Zscaler Private Access (ZPA) logs with Zscaler's Log Streaming Service (LSS) to Cribl Stream. Note: this guide only covers the mTLS portion of the Source setup.
Steps
1. Create a custom root CA with its corresponding private key (you could use tools like openssl or XCA for windows).
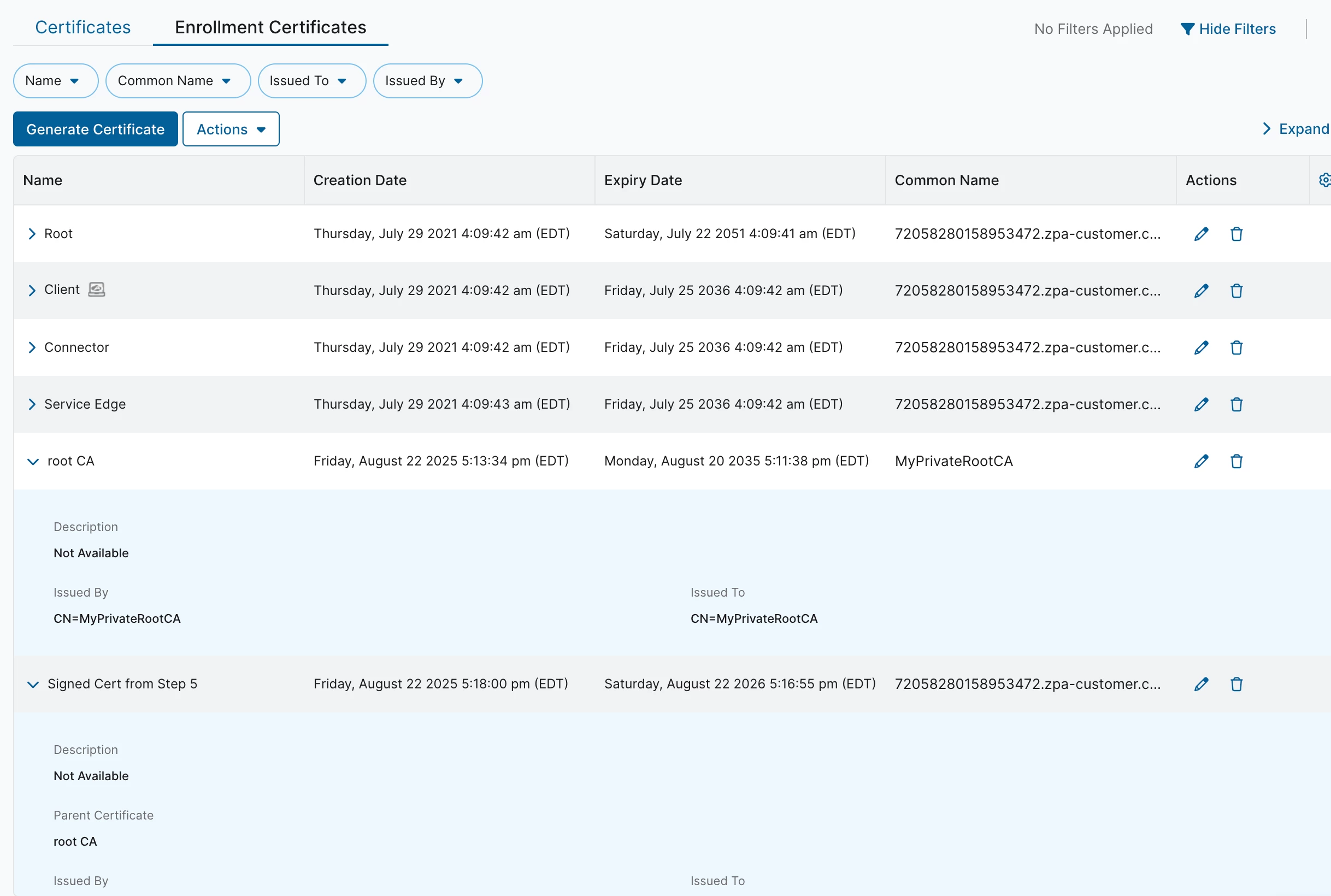
2. Import this root CA to ZPA Admin Portal: go to Configuration & Control -> Certificate Management -> Enrollment Certificates -> Upload Certificate Chain.
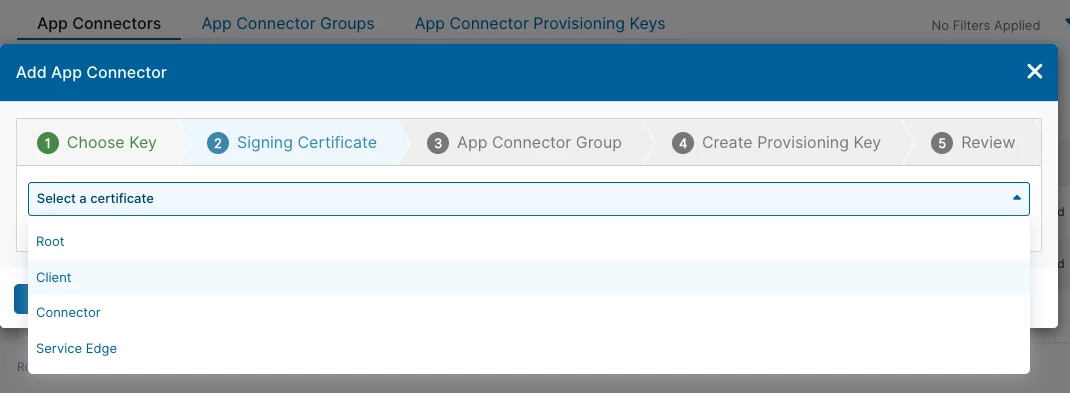
3. From ZPA Enrollment Certificates (same path as above), choose "Create a CSR".
4. Download the CSR and sign it with the custom root CA created on step 1. This certificate should have the constraint "CA:TRUE".
5. Import the signed certificate into ZPA the same way the root CA was imported in step 2. This will be the certificate used for app connector enrollment.
6. Deploy your app connector with the signed certificate imported in the previous step. See here for more information based on your platform.
7. Configure your log receiver for the LSS that sends to Cribl to use the app connector deployed in the previous step.
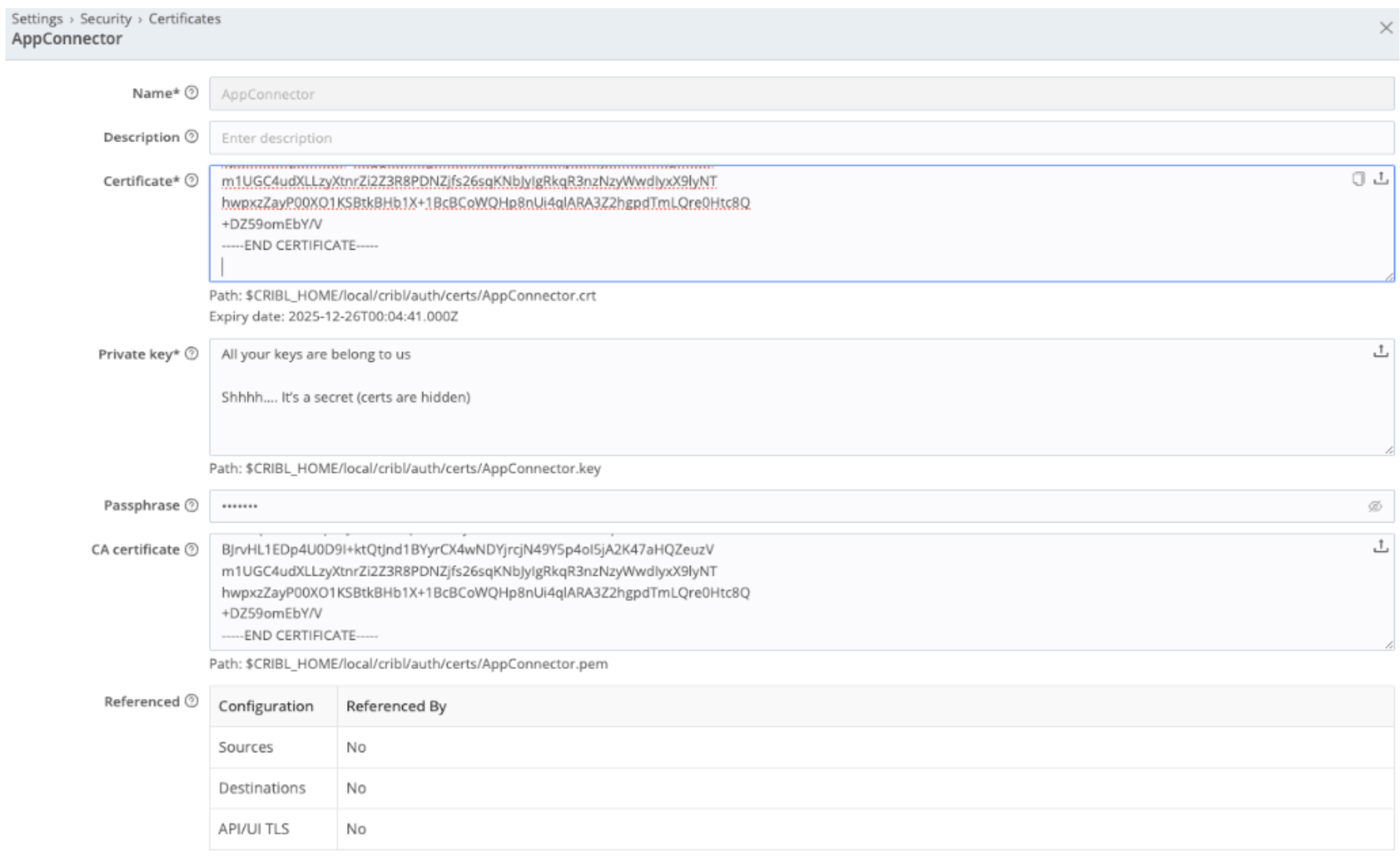
8. In Cribl Stream, in the correct Worker Group, go to Group Settings -> Security -> Certificates -> Add certificate.
9. Add the root CA created on step 2 under “Certificate” and also under “CA certificate”. Add its private key and the passphrase for the private key if encrypted.
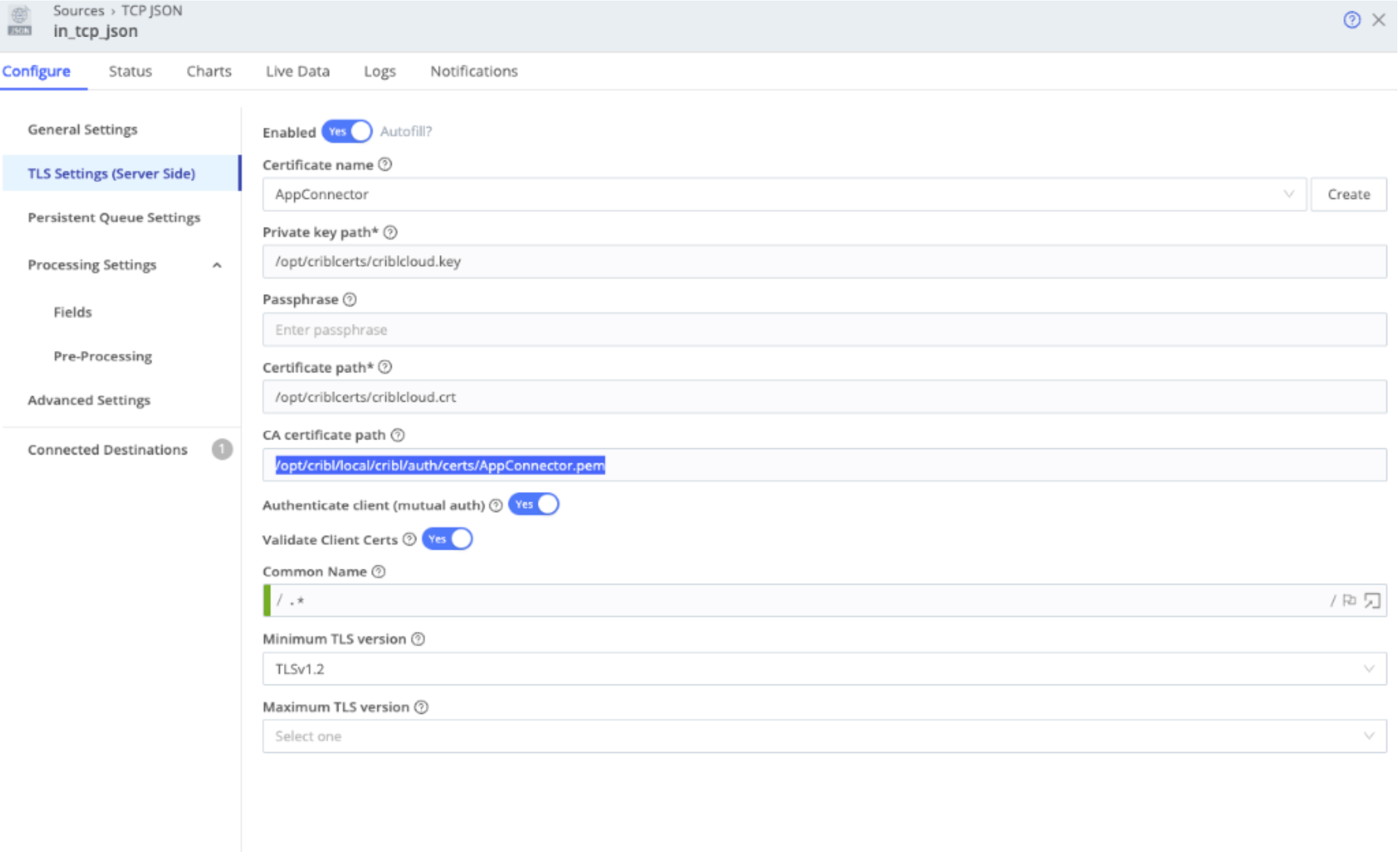
10. Next, go to Data -> Sources -> and open your source (in this example, TCP JSON) and configure and enable its TLS settings as below:
- Private key path and Certificate path will be left with default preconfigured values
- CA certificate path will be /opt/cribl/local/cribl/auth/certs/AppConnector.pem, where AppConnector.pem is the name given to the certificate added in step 9 .
11. Save the changes, then Commit and Deploy.
Additional Resources
For example videos for installing openssl and creating a custom private CA on Windows: